 Once you've determined the type of desktop system you want--a compact PC, a budget system, a mainstream all-purpose model, or a performance crackerjack--you need to know what components to look for. The processor and graphics chip you choose will determine many of your machine's capabilities, as will the system's memory and hard drive. Understanding those components will help you get the performance you need, without paying for things you don't.
Once you've determined the type of desktop system you want--a compact PC, a budget system, a mainstream all-purpose model, or a performance crackerjack--you need to know what components to look for. The processor and graphics chip you choose will determine many of your machine's capabilities, as will the system's memory and hard drive. Understanding those components will help you get the performance you need, without paying for things you don't.You'll also want to consider details like the layout of the case, which can also make the difference between a pleasant workstation and a nightmare PC.
Processor
The CPU is one of your PC's most important components. The processor you choose is likely to determine your PC's shape and size, and will definitely determine its price. Generally, the higher the CPU clock speed, the faster the performance you may see--and the higher the price. A 3.46GHz Core i5-670 PC will trounce a 2.93GHz Core i3-530 system, but you'll pay nearly twice as much for the faster CPU. Another spec to watch is cache size: More is better, here: Core i3 and Core i5 parts have 4MB caches, while performance-geared Core i7 chips have 6MB or 8MB caches.
Compact PCs and some all-in-ones use relatively puny netbook or notebook processors. Though these CPUs deliver weaker performance than desktop processors, they're also smaller and generate less heat, which makes them ideal for small machines. A PC packing an Atom processor should be fine for basic word processing, Web surfing, and limited media playback--but little more.
Intel's new Clarkdale line of Core i3 and Core i5 desktop processors tend to appear on systems in the budget desktop and mainstream desktop PC categories. Most users will find something they like in the Core i3 and Core i5 lines, as these CPUs offer dual-core performance at palatable price points. Core i3 chips are the cheaper, lower-powered models, so you'll generally find them in cheaper machines. The quad-core Core i7 targets users who need a real workhorse processor. If you play high-end games or edit hours of audio or video, you'll benefit from the Core i7. The lowliest Core i3 CPU can easily handle basic computing tasks, so stay within a reasonable price range when possible. At the lowest end are dual-core Pentium and Celeron processors. These chips appear in budget PCs, where price tags starting at $400 compensate for weaker performance.
Desktop PCs use either Intel or AMD processors. Intel currently holds the performance crown, but AMD has priced its dual- and quad-core chips aggressively. If you're looking for quad-core performance on a budget, AMD-based offerings are certainly worth a look.
Compact PCs and some all-in-ones use relatively puny netbook or notebook processors. Though these CPUs deliver weaker performance than desktop processors, they're also smaller and generate less heat, which makes them ideal for small machines. A PC packing an Atom processor should be fine for basic word processing, Web surfing, and limited media playback--but little more.
Intel's new Clarkdale line of Core i3 and Core i5 desktop processors tend to appear on systems in the budget desktop and mainstream desktop PC categories. Most users will find something they like in the Core i3 and Core i5 lines, as these CPUs offer dual-core performance at palatable price points. Core i3 chips are the cheaper, lower-powered models, so you'll generally find them in cheaper machines. The quad-core Core i7 targets users who need a real workhorse processor. If you play high-end games or edit hours of audio or video, you'll benefit from the Core i7. The lowliest Core i3 CPU can easily handle basic computing tasks, so stay within a reasonable price range when possible. At the lowest end are dual-core Pentium and Celeron processors. These chips appear in budget PCs, where price tags starting at $400 compensate for weaker performance.
Desktop PCs use either Intel or AMD processors. Intel currently holds the performance crown, but AMD has priced its dual- and quad-core chips aggressively. If you're looking for quad-core performance on a budget, AMD-based offerings are certainly worth a look.
Memory
If you use your computer for little more than light Web browsing and e-mail, 2GB of RAM will be enough, whether the system has Windows XP or Windows 7. More RAM will allow you to run more programs simultaneously, and generally improve the speed and performance of your machine. Systems today typically come with at least 4GB of RAM, though some small PCs and budget systems may be limited to 2GB or 3GB.
If you tend to multitask or play games, you'll want at least 4GB of RAM. If you play graphics-intensive games or do serious video or image editing, you might want to spring for even more RAM-some performance systems include 8GB or even 16GB of memory.
When you shop for RAM, you'll notice two types: DDR2 and DDR3. Of the two, DDR3 is faster and thus more expensive. You'll also notice a clock speed, much like processors, presented in MHz. Again, higher numbers are better. That said, quantifying the differences isn't easy; and if you're on a budget, 4GB of DDR2 RAM won't leave you at much of a disadvantage versus DDR3. In general, buy as much memory as you can afford. If you have to choose between getting more RAM at a slower clock speed and getting less RAM at a faster clock speed, you'll see more tangible results
with the greater amount of RAM. If you want to buy more than 4GB of RAM, make sure that the system ships with Microsoft's 64-bit Windows 7 operating system; a 32-bit OS will recognize only a little more than 3GB of whatever RAM your system has. If you purchase a new machine, it will probably come bundled with a 64-bit OS, as more retailers move toward including 4GB of RAM. Budget systems are the most likely to lean toward a 32-bit OS--but even there we've seen a shift to 64-bit, so if you decide to upgrade your system memory later, the operating system will be able to handle it. If you intend to upgrade your PC yourself, make sure that your system's motherboard can support additional RAM modules. Check your computer's specs to see how many user-accessible DIMM connectors are available; this information can be found on a system's technical specifications page. Our how-to guide on installing more memory will help you along the way.
If you tend to multitask or play games, you'll want at least 4GB of RAM. If you play graphics-intensive games or do serious video or image editing, you might want to spring for even more RAM-some performance systems include 8GB or even 16GB of memory.
When you shop for RAM, you'll notice two types: DDR2 and DDR3. Of the two, DDR3 is faster and thus more expensive. You'll also notice a clock speed, much like processors, presented in MHz. Again, higher numbers are better. That said, quantifying the differences isn't easy; and if you're on a budget, 4GB of DDR2 RAM won't leave you at much of a disadvantage versus DDR3. In general, buy as much memory as you can afford. If you have to choose between getting more RAM at a slower clock speed and getting less RAM at a faster clock speed, you'll see more tangible results
with the greater amount of RAM. If you want to buy more than 4GB of RAM, make sure that the system ships with Microsoft's 64-bit Windows 7 operating system; a 32-bit OS will recognize only a little more than 3GB of whatever RAM your system has. If you purchase a new machine, it will probably come bundled with a 64-bit OS, as more retailers move toward including 4GB of RAM. Budget systems are the most likely to lean toward a 32-bit OS--but even there we've seen a shift to 64-bit, so if you decide to upgrade your system memory later, the operating system will be able to handle it. If you intend to upgrade your PC yourself, make sure that your system's motherboard can support additional RAM modules. Check your computer's specs to see how many user-accessible DIMM connectors are available; this information can be found on a system's technical specifications page. Our how-to guide on installing more memory will help you along the way.
Desktop Case
A good case can make your everyday work easier and can simplify such tasks as upgrading and servicing components in a workplace. A well-designed case provides tool-less access to the interior, hard drives mounted on easy-to-slide-out trays, readily accessible USB ports and memory card slots, and color-coded cables for internal and external parts.
The most common cases are minitower and tower designs that use ATX. The ATX specification dictates where the connectors on the back of the motherboard should be (to line up with the holes in the case), and encompasses details such as the power-supply connector.
Slimline systems and other smaller PCs may use Micro-ATX, which follows the basic ATX specification but includes fewer expansion slots. Mini-ITX is smaller still; Mini-ITX motherboards often appear in small PCs, where they offer quiet, low-power performance (making these systems a great choice for a home-theater PCs).
If you're purchasing a minitower or tower system, you may have more flexibility in configuring it, whether you want to specify optional components to fill the slots or leave room for future expansion. You should reserve at least a couple of open hard drive bays and a free PCI slot, too. And since motherboards come in different shapes and sizes, so do case designs.
If you're buying an all-in-one or small PC or ordering a traditional tower from a major vendor such as HP or Dell, you rarely have much of a say in your machine's chassis. If the case's size and weight are important to you, try to inspect the machine in a store, or take note of its dimensions when shopping online.
The most common cases are minitower and tower designs that use ATX. The ATX specification dictates where the connectors on the back of the motherboard should be (to line up with the holes in the case), and encompasses details such as the power-supply connector.
Slimline systems and other smaller PCs may use Micro-ATX, which follows the basic ATX specification but includes fewer expansion slots. Mini-ITX is smaller still; Mini-ITX motherboards often appear in small PCs, where they offer quiet, low-power performance (making these systems a great choice for a home-theater PCs).
If you're purchasing a minitower or tower system, you may have more flexibility in configuring it, whether you want to specify optional components to fill the slots or leave room for future expansion. You should reserve at least a couple of open hard drive bays and a free PCI slot, too. And since motherboards come in different shapes and sizes, so do case designs.
If you're buying an all-in-one or small PC or ordering a traditional tower from a major vendor such as HP or Dell, you rarely have much of a say in your machine's chassis. If the case's size and weight are important to you, try to inspect the machine in a store, or take note of its dimensions when shopping online.
Operating System
It may be a decade old, but Windows XP remains a stalwart--even on some new systems. Nevertheless, most systems on the market today run Windows 7. Microsoft's latest operating system has received generally positive reviews, improving on many of Windows Vista's foibles.
Microsoft sells six different versions of Windows 7, but only three--Windows 7 Home Premium, Windows 7 Professional, and Windows 7 Ultimate--are available to most desktop buyers. Windows 7 Home Premium, the standard offering, includes the visually appealing Aero Glass UI, plus enhancements to Windows Media Center. Advanced users should consider Windows 7 Professional, typically a $75 to $100 step up; it offers location-aware printing and improved security features that many business users like. Windows 7 Ultimate--which costs about $150 more--is a good choice for power users and business users, thanks to its wealth of networking and encryption tools. Consult a full list of OS features before settling on a particular version.
Once again, if you're running a 32-bit operating system, your computer can use only slightly more than 3GB of RAM, regardless of how much your system carries. So be sure to pick a 64-bit OS; you'll be glad you did when you're ready to upgrade.
Microsoft sells six different versions of Windows 7, but only three--Windows 7 Home Premium, Windows 7 Professional, and Windows 7 Ultimate--are available to most desktop buyers. Windows 7 Home Premium, the standard offering, includes the visually appealing Aero Glass UI, plus enhancements to Windows Media Center. Advanced users should consider Windows 7 Professional, typically a $75 to $100 step up; it offers location-aware printing and improved security features that many business users like. Windows 7 Ultimate--which costs about $150 more--is a good choice for power users and business users, thanks to its wealth of networking and encryption tools. Consult a full list of OS features before settling on a particular version.
Once again, if you're running a 32-bit operating system, your computer can use only slightly more than 3GB of RAM, regardless of how much your system carries. So be sure to pick a 64-bit OS; you'll be glad you did when you're ready to upgrade.
Graphics Cards
The GPU (graphics processing unit) is responsible for everything you see on your display, whether you play games, watch videos, or just stare at the Aero desktop baked into Windows 7.
If you aren't interested in gaming on your PC, integrated graphics built onto the motherboard--or in the CPU itself with Intel's new Core i3 and Core i5 Clarkdale chips--is the way to go. Integrated graphics help keep a system's cost low, and they deliver enough power to run simple games or high-definition Flash video. Intel's integrated graphics chips are widely used, but some PCs include an nVidia Ion graphics chip, which offers superior integrated video performance.
If you plan to render your own high-definition content or play BioShock 2, you'll need a discrete graphics card. Such cards come installed in a PCIe x16 slot on your motherboard and deliver significantly more power than integrated graphics do. Both ATI and nVidia offer plenty of options to choose from. The naming conventions can be a bit overwhelming, but the rule of thumb is that higher numbers indicate better performance--and higher prices.
Variables such as power consumption, size, and the brand of your motherboard (which may limit which cards you can use) help determine which GPU is right for you.
Gamers with deep pockets can opt for a multiple-graphics-card setup using either nVidia's SLI or ATI's CrossFire technology, either of which sets multiple cards to work in tandem for vastly improved performance. That performance will cost you, however: Prices for higher-end graphics cards generally range between $200 and $400 for apiece.
Hard Drive
If you aren't interested in gaming on your PC, integrated graphics built onto the motherboard--or in the CPU itself with Intel's new Core i3 and Core i5 Clarkdale chips--is the way to go. Integrated graphics help keep a system's cost low, and they deliver enough power to run simple games or high-definition Flash video. Intel's integrated graphics chips are widely used, but some PCs include an nVidia Ion graphics chip, which offers superior integrated video performance.
If you plan to render your own high-definition content or play BioShock 2, you'll need a discrete graphics card. Such cards come installed in a PCIe x16 slot on your motherboard and deliver significantly more power than integrated graphics do. Both ATI and nVidia offer plenty of options to choose from. The naming conventions can be a bit overwhelming, but the rule of thumb is that higher numbers indicate better performance--and higher prices.
Variables such as power consumption, size, and the brand of your motherboard (which may limit which cards you can use) help determine which GPU is right for you.
Gamers with deep pockets can opt for a multiple-graphics-card setup using either nVidia's SLI or ATI's CrossFire technology, either of which sets multiple cards to work in tandem for vastly improved performance. That performance will cost you, however: Prices for higher-end graphics cards generally range between $200 and $400 for apiece.
Hard Drive
Even a basic full-size PC should offer at least 320GB of hard drive space. Small PCs, however, tend to start around 160GB. At the upper end of the performance spectrum, power PCs may offer space for 2TB of storage--or more--along with choices of RAID for data redundancy (RAID 1) or speed optimization (RAID 0), or an option to combine a solid-state drive with a hard drive.
When shopping for a PC, check the specifications to see how many internal 2.5-inch hard drive bays are available.
Many all-in-one and small PCs limit you to just one. But with additional internal hard drives, you can store more data and create RAID arrays to safeguard your data from hardware failure, deliver faster performance, or do both. Most drives today are Serial ATA-300 models, which spin at 7200 rpm. When shopping, pay close attention to the speed of the PC's hard drive: Small PCs may use 2.5-inch hard drives that spin at 5400 rpm, and the potential money savings may not justify the performance hit if you plan to do a lot disk-intensive tasks. For people who care more about speed than about capacity, Western Digital's VelociRaptor line offers 10,000-rpm drives, though these max out at 300GB.
Another option for speed-conscious buyers is a solid state drive. The cost-per-gigabyte is still far greater for SSDs than for traditional hard drives, but prices have come down, and performance has improved. Some PC makers offering an SSD in tandem with a hard-disk drive--a low-capacity SSD to store applications and the OS, and a high-capacity HDD for data storage duties.
When shopping for a PC, check the specifications to see how many internal 2.5-inch hard drive bays are available.
Many all-in-one and small PCs limit you to just one. But with additional internal hard drives, you can store more data and create RAID arrays to safeguard your data from hardware failure, deliver faster performance, or do both. Most drives today are Serial ATA-300 models, which spin at 7200 rpm. When shopping, pay close attention to the speed of the PC's hard drive: Small PCs may use 2.5-inch hard drives that spin at 5400 rpm, and the potential money savings may not justify the performance hit if you plan to do a lot disk-intensive tasks. For people who care more about speed than about capacity, Western Digital's VelociRaptor line offers 10,000-rpm drives, though these max out at 300GB.
Another option for speed-conscious buyers is a solid state drive. The cost-per-gigabyte is still far greater for SSDs than for traditional hard drives, but prices have come down, and performance has improved. Some PC makers offering an SSD in tandem with a hard-disk drive--a low-capacity SSD to store applications and the OS, and a high-capacity HDD for data storage duties.
Networking
The days of dial-up are done. Broadband speed and performance vary by service provider and location, but you can maximize your PC's connectivity by choosing the right networking options. Fortunately, the options are clear-cut: wired or wireless.
Every system comes with a wired ethernet connection--at least 10/100 ethernet, and more often gigabit ethernet. Wireless connectivity is an attractive option for small PCs and all-in-ones, but also for some tower and minitower systems (though you'll need only if your system will be nowhere near your router). If you'd rather not tie down your otherwise svelte machine with an ethernet cable, go wireless and opt for 802.11n; this wireless standard offers better performance than the older 802.11b/g standards.
Wireless performance still has limitations. If you plan to use your PC to stream high-definition Internet content from sites like Hulu and Netflix, consider using a wired connection for best performance. You'll get measurably superior performance, and you'll future-proof your machine in case you later upgrade to network-attached machines with faster transfer speeds.
Every system comes with a wired ethernet connection--at least 10/100 ethernet, and more often gigabit ethernet. Wireless connectivity is an attractive option for small PCs and all-in-ones, but also for some tower and minitower systems (though you'll need only if your system will be nowhere near your router). If you'd rather not tie down your otherwise svelte machine with an ethernet cable, go wireless and opt for 802.11n; this wireless standard offers better performance than the older 802.11b/g standards.
Wireless performance still has limitations. If you plan to use your PC to stream high-definition Internet content from sites like Hulu and Netflix, consider using a wired connection for best performance. You'll get measurably superior performance, and you'll future-proof your machine in case you later upgrade to network-attached machines with faster transfer speeds.
Keyboard and Mouse
Your keyboard and mouse are crucial devices, so get a set that works for you. But if you're buying a PC online, don't pay the upgrade price that the vendor offers: You can usually get a better deal by shopping around. If you aren't sure what your keyboard or a mouse options are, visit your local PC or electronics retailer and try out a few of the display models.
Most physical attributes of keyboards and mice vary from user to user, so keep in mind where and how you'll be using your machine. Every system comes with at least a basic mouse and keyboard. At build-to-order PC sites, though, you usually have relatively few options. If you plan to use a small PC to stream media, consider a small, lightweight wireless keyboard and mouse combo--or a wireless keyboard with built-in pointing device--so you can operate it from the comfort of a couch. Wireless keyboards and mice use either radio-frequency (RF) or Bluetooth technology, and require you to plug a USB receiver into a USB port on your machine. When shopping for a keyboard, watch for handy media keys. These put media playback buttons and volume controls on your keyboard, heightening the couch-based computing experience. If you plan to buy a tower PC, you'll likely have space on your desk for a full-size keyboard with number pad. If comfort is an issue or you struggle with wrist pain, look for ergonomic keyboards and mice that conform to the shape of your hands, and workspace. If you're an avid gaming fan, consider keyboards and mice from brands like
Razer and Logitech that offer backlit keys, programmable macro buttons, and other features that may give you a competitive edge.
Most physical attributes of keyboards and mice vary from user to user, so keep in mind where and how you'll be using your machine. Every system comes with at least a basic mouse and keyboard. At build-to-order PC sites, though, you usually have relatively few options. If you plan to use a small PC to stream media, consider a small, lightweight wireless keyboard and mouse combo--or a wireless keyboard with built-in pointing device--so you can operate it from the comfort of a couch. Wireless keyboards and mice use either radio-frequency (RF) or Bluetooth technology, and require you to plug a USB receiver into a USB port on your machine. When shopping for a keyboard, watch for handy media keys. These put media playback buttons and volume controls on your keyboard, heightening the couch-based computing experience. If you plan to buy a tower PC, you'll likely have space on your desk for a full-size keyboard with number pad. If comfort is an issue or you struggle with wrist pain, look for ergonomic keyboards and mice that conform to the shape of your hands, and workspace. If you're an avid gaming fan, consider keyboards and mice from brands like
Razer and Logitech that offer backlit keys, programmable macro buttons, and other features that may give you a competitive edge.
Removable Storage
Your operating system and system restore disks (if any) will still ship on a DVD; consequently all but a handful of small PCs ship with a dual-layer multiformat DVD burner. If you're a fan of high-definition media, consider adding a Blu-ray reader/DVD burner combo drive to store data on your own CDs and DVDs and to watch media stored on Blu-ray discs. To take advantage of the massive storage opportunities offered by Blu-ray discs, you'll need a Blu-ray writer--add-on that lets you read and write in every disc-based media format. HP and other companies market portable media drives, ranging from less than $100 to as high as $250. These hard-drive models work with a USB cable, but are designed to slide into a media drive bay included on select desktop models. Portable hard drives are and crucial to anyone who wants to protect data from hard-drive failure or to transport lots of content. Consult our "Top 10 Portable Hard Drives" chart for further options.
Sound
Sound
The integrated sound provided on a typical PC's motherboard today supports 5.1-channel audio. This should suffice for users who don't want to spend a lot of money on their PC's audio system. But a dedicated sound card will improve the dynamic range of compressed audio, add rich environmental effects to games, and improve system performance when you record or mix audio.
On most PCs above the budget level, motherboards come with 7.1-channel audio. If you're shopping for a PC with integrated graphics, look for models sporting the nVidia Ion graphics processor, which also offers 7.1-channel HD audio.
A sound card can increase your PC's initial cost by $40 to $80, depending on the technology that the card uses. Higher-end cards can cost more than $200, but these generally target creative professionals or gamers who require 3D environmental audio effects for competitive play.
If you do opt for a sound card, make sure that your motherboard has a spare PCI or PCI-Express slot, depending on the requirements of the card that you've chosen. The manufacturer's specifications for the machine or motherboard you're buying will list the slots it has available.
As with all upgrade options, comparison-shop before you settle on a particular sound card or set of speakers. You may find a better deal elsewhere. On the other hand, if you buy the card yourself, you'll have to crack open your system to install the card.
Speaker preferences are personal, and the physical dimensions of the room your computer is in may limit your options. PCs of all shapes and sizes have analog audio outputs, and some models include a digital optical connection, which reduces the number of cables you need.
Many all-in-one PCs include a speaker bar attached to the screen. Audio from these sound bars varies from model to model, but in general the quality will be akin to that of laptop speakers, with deeper, richer sound from more-expensive models. If sound quality isn't a high priority, the included speaker bar will perform adequately, just as built-in speakers usually suffice for an HDTV. But if you plan to use your all-in-one as a primary media machine, we recommend choosing dedicated speakers with a subwoofer.
On most PCs above the budget level, motherboards come with 7.1-channel audio. If you're shopping for a PC with integrated graphics, look for models sporting the nVidia Ion graphics processor, which also offers 7.1-channel HD audio.
A sound card can increase your PC's initial cost by $40 to $80, depending on the technology that the card uses. Higher-end cards can cost more than $200, but these generally target creative professionals or gamers who require 3D environmental audio effects for competitive play.
If you do opt for a sound card, make sure that your motherboard has a spare PCI or PCI-Express slot, depending on the requirements of the card that you've chosen. The manufacturer's specifications for the machine or motherboard you're buying will list the slots it has available.
As with all upgrade options, comparison-shop before you settle on a particular sound card or set of speakers. You may find a better deal elsewhere. On the other hand, if you buy the card yourself, you'll have to crack open your system to install the card.
Speaker preferences are personal, and the physical dimensions of the room your computer is in may limit your options. PCs of all shapes and sizes have analog audio outputs, and some models include a digital optical connection, which reduces the number of cables you need.
Many all-in-one PCs include a speaker bar attached to the screen. Audio from these sound bars varies from model to model, but in general the quality will be akin to that of laptop speakers, with deeper, richer sound from more-expensive models. If sound quality isn't a high priority, the included speaker bar will perform adequately, just as built-in speakers usually suffice for an HDTV. But if you plan to use your all-in-one as a primary media machine, we recommend choosing dedicated speakers with a subwoofer.





 So what is grid? Here's a three-part checklist. According to this checklist, a grid:
So what is grid? Here's a three-part checklist. According to this checklist, a grid: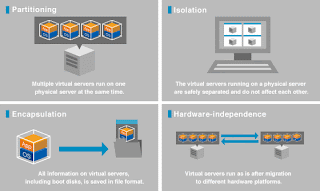
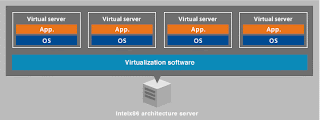

 Cabling
Cabling Managed Switches
Managed Switches





